eID Box
Our secure digital middleware solution, the eID Box, streamlines smart card integration with applications through standardized interfaces.
As a result, it ensures access to features such as e-signatures and authentication for third-party applications, whether they operate online or offline.
By leveraging cloud solutions and custom software development, eID Box offers a versatile solution for electronic identity applications, enabling seamless integration with various cryptographic tokens using standardized APIs.
eIDBox - Unpack your identity
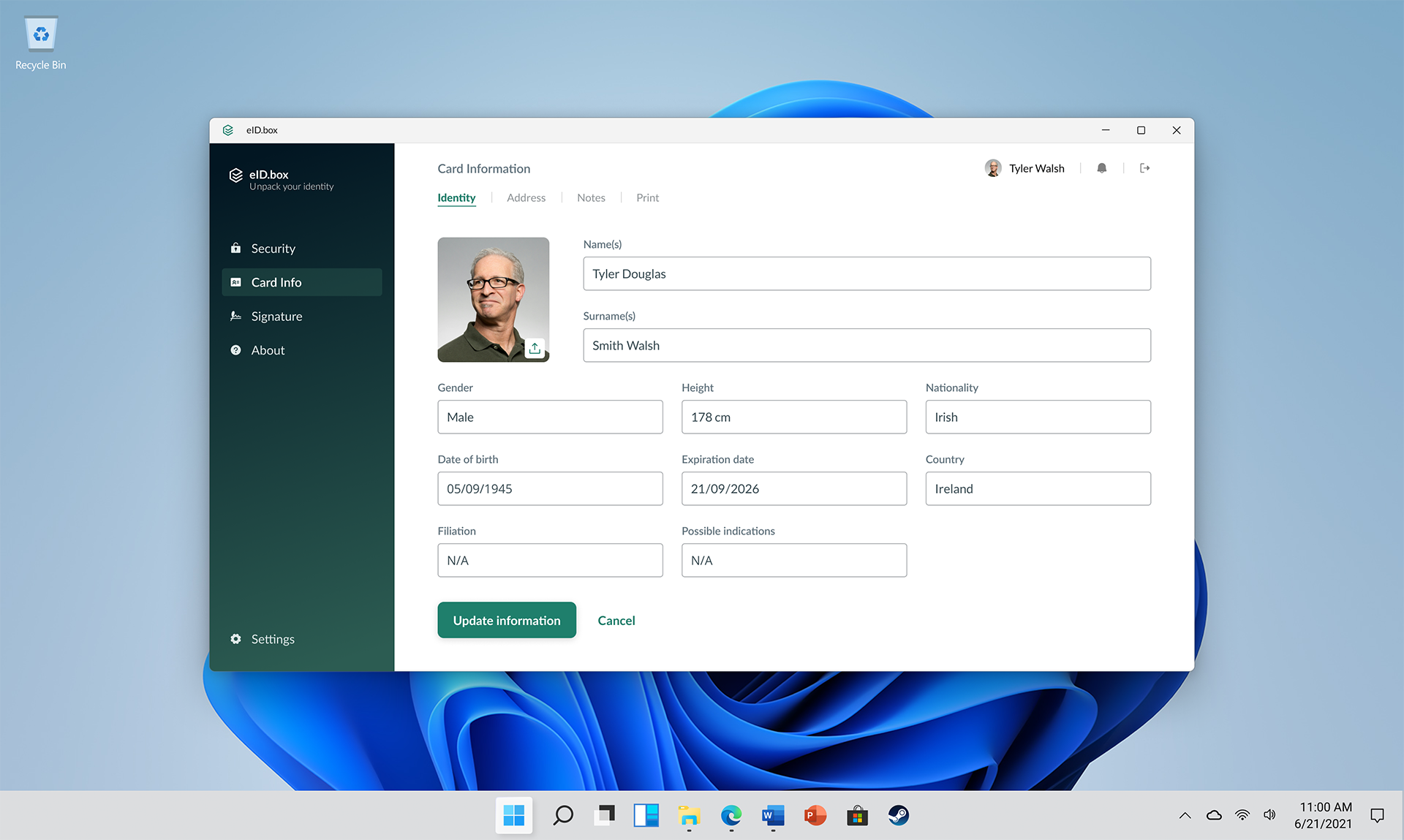
Our secure digital middleware solution empowers users to efficiently manage all card objects, including PINs, PUKs, certificates and personal data, providing comprehensive control over their cryptographic tokens. Consequently, it enables you to securely sign documents and perform cryptographic operations, ensuring robust security.
Available for Windows, Linux, MacOS, iOS and Android, it integrates with the most common platforms, ensuring accessibility across a wide range of devices.
eID GUI Applications
In conjunction with the eID Server subsystem, this module extends access to eIDAS token functionalities found in ID cards. This includes capabilities like genre verification, address verification, age verification, restricted identification and ID attribute sharing.
Desktop and Mobile SDK Modules
Our SDK modules seamlessly collaborate with the eID server subsystem, allowing e-signature and eID functions to be readily available on Windows, Linux, MacOS. It is also available for iOS and Android equipped with NFC interfaces.
Features of our Secure Digital Middleware Solution
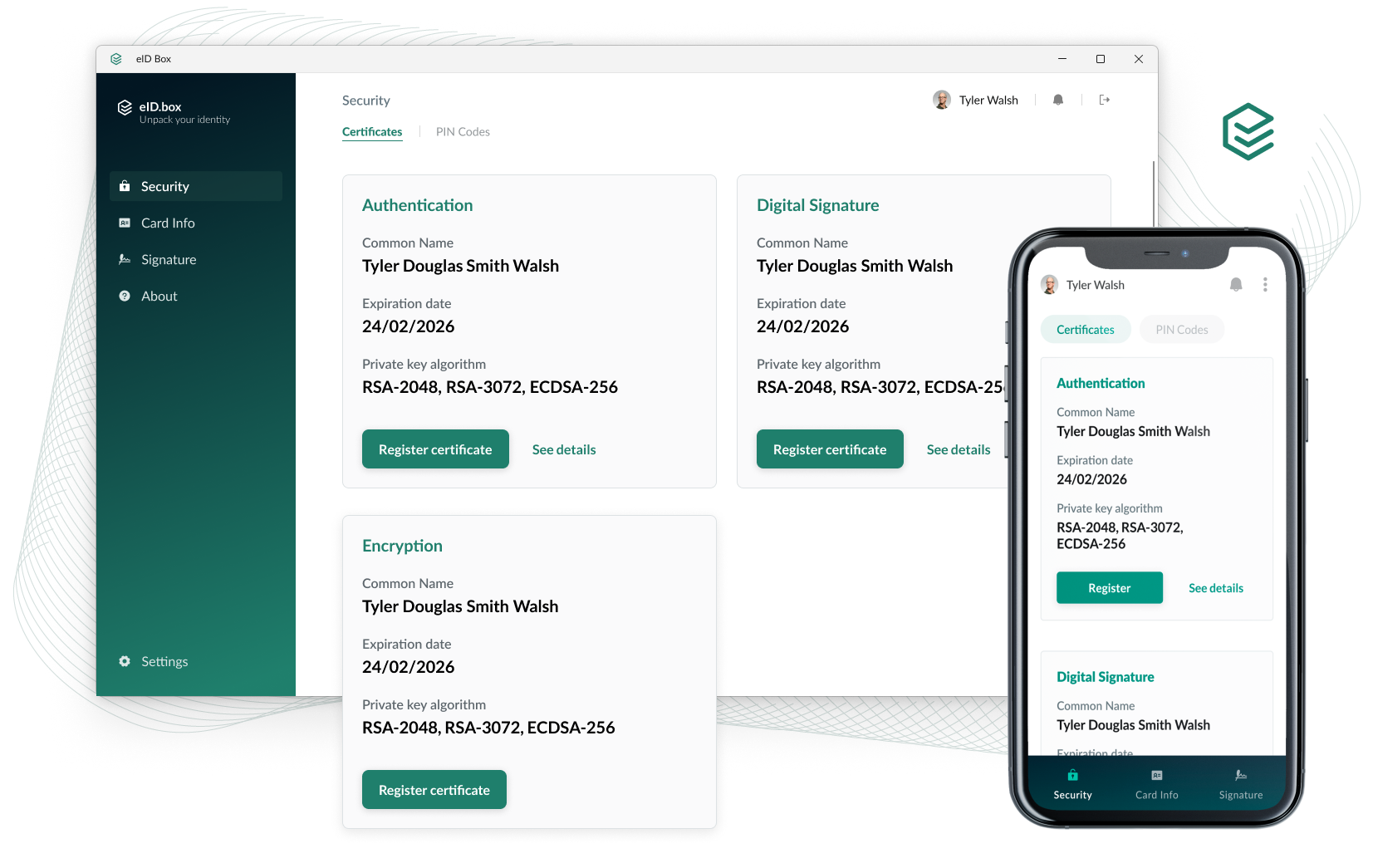
This middleware solution allows generic applications to utilize smart card features through operating system standard interfaces. The following features demonstrate how the eID Box improves security and enhances user experience:
- PACE-enabled eID integration for smart cards
- Verify and access smart card data
- Activate custom app functionalities
- PIN management for security
- Standardized token modules
- Seamlessly integrate with OS and apps
Available modules
Desktop GUI Application
Cross-platform desktop application that reads and manages cardholder data from ID cards
Desktop Installer
Installer that simplifies the setup of our middleware solution, compatible with Windows, Linux, and MacOS
Desktop SDK
Allow custom applications to use all card features (sign documents, activate card, read card data, write card data, verify certificates)
Mobile SDK
Seamlessly collaborates with the eID server, allowing e-signature and eID functions to be readily available on mobile
Minidriver: CryptoAPI card module
Allows you to securely manage cryptographic operations, cryptographic keys, and access card features
CNG Key Storage Provider module for a remote QSCD
Ensures that desktop applications can harness the power of remote QSCD for document signing
PKCS#11 module for Windows, Linux and MacOS
Your applications can securely sign documents and perform cryptographic operations
CryptoTokenKit module for MacOS
Empowers you to manage keys, protect data, and ensure secure access.